The Easiest Tunnel Ever
From DD-WRT Wiki
| Revision as of 11:16, 18 September 2019 (edit) Mile-Lile (Talk | contribs) ← Previous diff |
Revision as of 21:01, 16 January 2020 (edit) (undo) Jeremywh7 (Talk | contribs) (Integrated with the main wiki so it points here for the setup, since this one is referenced -everywhere-) Next diff → |
||
| Line 1: | Line 1: | ||
| + | [[VPN]] -> [[Wireguard]] -> '''[[The Easiest Tunnel Ever]]'''<br> | ||
| + | |||
| + | __TOC__ | ||
| + | |||
| + | |||
| =Introduction= | =Introduction= | ||
| - | This [[Wireguard]] | + | This [[Wireguard]] guide will show you the basics of creating tunnel from a client device to DD-WRT unit in a secure way. Before proceeding, verify a working reset button and configuration backup in case of problems. |
| - | + | ||
| - | + | [[Image:oet1.PNG|600px|Instructions]] | |
| - | [[Image:oet1.PNG| | + | |
| [[Image:QR-Code.PNG|thumbnail|Instructions]] | [[Image:QR-Code.PNG|thumbnail|Instructions]] | ||
| [[Image:Android.jpeg|thumbnail|Instructions]] | [[Image:Android.jpeg|thumbnail|Instructions]] | ||
| [[Image:Enable.jpeg|thumbnail|Instructions]] | [[Image:Enable.jpeg|thumbnail|Instructions]] | ||
| [[Image:DecodeQRcode.PNG|thumbnail|Instructions]] | [[Image:DecodeQRcode.PNG|thumbnail|Instructions]] | ||
| - | [[Image:Vpn.jpg|thumbnail|Instructions]] | ||
| - | [[Image:Blabla.png|thumbnail|Instructions]] | ||
| - | |||
| - | ==Why WireGuard?== | ||
| - | [https://www.wireguard.com/ WireGuard®] is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. | ||
| - | It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. | ||
| - | It intends to be considerably more performant than OpenVPN. | ||
| ==Why WireGuard + DD-WRT tunnel?== | ==Why WireGuard + DD-WRT tunnel?== | ||
| - | Starting | + | Starting since build 38581 in February 2019, a client config can be imported using QR Code. The advantage of this approach is that there is no need to transfer sensitive information via data channels that can potentially be compromised |
| - | + | and there is no need of any other supplementary software besides WireGuard and the DD-WRT GUI. | |
| - | and there is no need of any other supplementary software besides | + | |
| ==What is a QR Code?== | ==What is a QR Code?== | ||
| Line 31: | Line 26: | ||
| =Instructions= | =Instructions= | ||
| ==Creating tunnel== | ==Creating tunnel== | ||
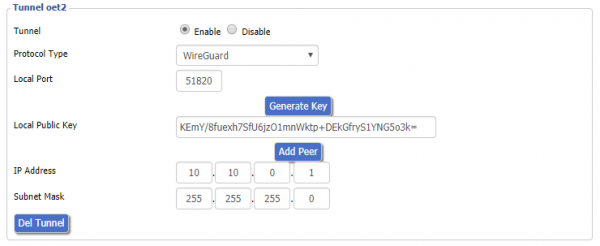
| - | First, enable the tunnel on the DD-WRT | + | First, enable the tunnel on the DD-WRT ''Basic'' -> ''Tunnels'' tab (eop-tunnel.asp). From the ''Protocol Type'' drop-down menu, choose WireGuard. Generate Key and enter IP Address (this will be oet1 interface ip and must be out of your local lan range, on a separate network. |
| - | From the ''Protocol Type'' drop-down menu, choose WireGuard. Generate Key and enter IP Address (this will be oet1 interface ip and must be out of your local lan range, on a separate network. | + | *E.g. if the router LAN IP is 192.168.2.1, for the oet1 IP address use 10.10.0.1. |
| - | E.g. if | + | |
| ==Adding Peer== | ==Adding Peer== | ||
| Line 39: | Line 33: | ||
| ==Masquerading tunnel== | ==Masquerading tunnel== | ||
| - | + | Wireguard cannot bridge anything, you always have use Forward and NAT. Go to Networking and unbridge the oet1 interface and enable Masquerade / NAT to have internet on other side of the tunnel. Click ''Apply''. | |
| - | + | ||
| - | ===Note for Access Point mode=== | + | ====Note for Access Point mode==== |
| Add the following firewall rule under Administration/Commands and save as firewall then reboot: | Add the following firewall rule under Administration/Commands and save as firewall then reboot: | ||
| <pre>iptables -t nat -I POSTROUTING -o br0 -j SNAT --to $(nvram get lan_ipaddr)</pre> | <pre>iptables -t nat -I POSTROUTING -o br0 -j SNAT --to $(nvram get lan_ipaddr)</pre> | ||
| Line 53: | Line 46: | ||
| [https://itunes.apple.com/us/app/wireguard/id1441195209 Apple iOS (iOS 12.0 or later)] | [https://itunes.apple.com/us/app/wireguard/id1441195209 Apple iOS (iOS 12.0 or later)] | ||
| - | ==Importing config to | + | ==Importing config to Linux== |
| - | + | These packages are needed: | |
| - | + | ||
| - | + | ||
| * networkmanager-wireguard-git (dkms) | * networkmanager-wireguard-git (dkms) | ||
| - | * | + | * A graphical QRCode decoder e.g. '''qtqr''' |
| - | + | * Screenshot tool e.g. [https://flameshot.js.org/#/ flameshot] | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | * | + | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | Review your distribution's wiki and forums for more specific details. | |
| + | *Go to the eop-tunnel.asp of your router, and grab a screenshot of the qrcode. | ||
| + | *Save it but remember location and name of png file. | ||
| + | *Open the qrcode decoder and add the png file to decode | ||
| + | *You will be prompted with a decoded txt config file. | ||
| + | *Use it to populate wireguard client side config in the network manager. | ||
| - | + | ==Importing config to Windows== | |
| + | Software: | ||
| + | * [https://www.wireguard.com/install/ Windows .msi installer] | ||
| + | * A graphical QRCode decoder e.g. [https://www.codetwo.com/freeware/qr-code-desktop-reader/ CodeTwo QR Code Reader] | ||
| - | + | [[Image:Vpn.jpg|400px|Instructions]] | |
| + | [[Image:Blabla.png|300px|Instructions]] | ||
| - | + | ==Reference== | |
| + | For more details and Troubleshooting see the parent [[Wireguard]] wiki<br> | ||
| + | For the latest updated information and additional scripts see the [https://forum.dd-wrt.com/phpBB2/viewtopic.php?t=322206 Wireguard setup guide]. | ||
| - | =Reference= | ||
| - | [https://www.wireguard.com/#conceptual-overview Conceptual Overview]<br> | ||
| - | [https://git.zx2c4.com/WireGuard/ Git Repository]<br> | ||
| - | [https://lists.zx2c4.com/mailman/listinfo/wireguard/ WireGuard Mailing Lists]<br> | ||
| - | [https://svn.dd-wrt.com/log/src/router/wireguard Changeset]<br> | ||
| - | [https://www.dd-wrt.com/phpBB2/viewtopic.php?t=312522 Forum]<br> | ||
| [[Category:Tunneling]] | [[Category:Tunneling]] | ||
| [[Category:Basic tutorials]] | [[Category:Basic tutorials]] | ||
Revision as of 21:01, 16 January 2020
VPN -> Wireguard -> The Easiest Tunnel Ever
Contents |
Introduction
This Wireguard guide will show you the basics of creating tunnel from a client device to DD-WRT unit in a secure way. Before proceeding, verify a working reset button and configuration backup in case of problems.
Why WireGuard + DD-WRT tunnel?
Starting since build 38581 in February 2019, a client config can be imported using QR Code. The advantage of this approach is that there is no need to transfer sensitive information via data channels that can potentially be compromised and there is no need of any other supplementary software besides WireGuard and the DD-WRT GUI.
What is a QR Code?
The QR Code is a two-dimensional version of the barcode, known from product packaging in the supermarket. Originally developed for process optimization in the logistics of the automotive industry, the QR Code has found its way into mobile marketing with the widespread adoption of smartphones. "QR" stands for "Quick Response", which refers to the instant access to the information hidden in the Code. QR Codes are gaining popularity because the technology is "open source", i.e. available for everyone. Significant advantages of QR Codes over conventional barcodes are larger data capacity and high fault tolerance.
Instructions
Creating tunnel
First, enable the tunnel on the DD-WRT Basic -> Tunnels tab (eop-tunnel.asp). From the Protocol Type drop-down menu, choose WireGuard. Generate Key and enter IP Address (this will be oet1 interface ip and must be out of your local lan range, on a separate network.
- E.g. if the router LAN IP is 192.168.2.1, for the oet1 IP address use 10.10.0.1.
Adding Peer
For a simple configuration you just need to enter Peer Tunnel IP within oet1 interface ip range (e.g. 10.10.0.2) and Peer Tunnel DNS (8.8.8.8). Peer Tunnel MTU will be calculated automatically (WAN mtu-40) but can then be edited. Click Save. Generate QR-Code by pressing QR-Code button.
Masquerading tunnel
Wireguard cannot bridge anything, you always have use Forward and NAT. Go to Networking and unbridge the oet1 interface and enable Masquerade / NAT to have internet on other side of the tunnel. Click Apply.
Note for Access Point mode
Add the following firewall rule under Administration/Commands and save as firewall then reboot:
iptables -t nat -I POSTROUTING -o br0 -j SNAT --to $(nvram get lan_ipaddr)
Importing config to Android/iOS
Start your WireGuard app. In lower right corner press "+" and select "Create from QR code", scan QO-Code within DD-WRT GUI (peer section). After transferring config file from dd-wrt you will be prompted to name your tunnel. Go to whats is my ip to check you public IP. Android Apple iOS (iOS 12.0 or later)
Importing config to Linux
These packages are needed:
- networkmanager-wireguard-git (dkms)
- A graphical QRCode decoder e.g. qtqr
- Screenshot tool e.g. flameshot
Review your distribution's wiki and forums for more specific details.
- Go to the eop-tunnel.asp of your router, and grab a screenshot of the qrcode.
- Save it but remember location and name of png file.
- Open the qrcode decoder and add the png file to decode
- You will be prompted with a decoded txt config file.
- Use it to populate wireguard client side config in the network manager.
Importing config to Windows
Software:
- Windows .msi installer
- A graphical QRCode decoder e.g. CodeTwo QR Code Reader
Reference
For more details and Troubleshooting see the parent Wireguard wiki
For the latest updated information and additional scripts see the Wireguard setup guide.