Separate LAN and WLAN
From DD-WRT Wiki
| Revision as of 18:00, 27 January 2007 (edit) 1169920083 (Talk | contribs) ← Previous diff |
Current revision (03:06, 28 September 2020) (edit) (undo) Tag (Talk | contribs) m (→Step 3: Controlling Access - Update syntax for NOT in iptables) |
||
| (83 intermediate revisions not shown.) | |||
| Line 1: | Line 1: | ||
| - | + | {{Languages|Separate LAN and WLAN}} | |
| - | + | __TOC__ | |
| - | == | + | ==Introduction== |
| - | + | This guide explains how to separate the wireless interface from the "LAN&WLAN" bridge so that they are on different subnets. You are then able to control communication between the interfaces using iptables commands. | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| + | If your router is configured as a [[Wireless Access Point]] (WAN is disabled) then you must be sure to set the gateway and local DNS as recommended in the WAP guide. This also applies to WDS client nodes (but not the main WDS node) which are bridged to another router that does routing for them. Keep your eye out for the places this guide gives alternative instructions for WAP's. | ||
| + | '''Note:''' If you're separating virtual interfaces then use the instructions from the [[Multiple_WLANs | Multiple WLAN Guide]]. | ||
| + | ==Preparation== | ||
| + | Go to the '''Administration -> Commands''' page, insert the command below, and press the '''Run Commands''' button to find out the actual name of your wl0 interface. If you have a wl1 interface that you want to unbridge then change the command accordingly. | ||
| + | nvram get wl0_ifname | ||
| + | == Configuration == | ||
| + | === Step 1: Remove the Wireless Interface from the LAN bridge === | ||
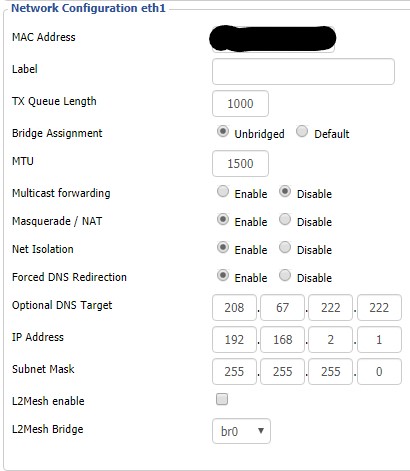
| + | 1. Navigate to the '''Setup -> Networking''' page.<br/> | ||
| + | 2. In the '''Port Setup''' section, find the configuration for the interface (identified in [[#Preparation]]) that you would like to unbridge.<br/> | ||
| + | 3. For that interface, select the '''Unbridged''' radio button next to '''Bridge Assignment'''. More options will appear.<br/> | ||
| + | 4. Set '''Masquerade / NAT''' to '''Enable'''.<br/> | ||
| + | 5. Set '''Net Isolation''' to '''Enable'''. This will automatically add a rule like this to your firewall: | ||
| + | iptables -I FORWARD -i <interface> --destination 192.168.1.0/24 -m state --state NEW -j DROP | ||
| + | 6. Set an '''IP Address''' that is in an unused subnet, e.g. '''192.168.2.1'''.<br/> | ||
| + | 7. Set the '''Subnet Mask''' to '''255.255.255.0'''.<br/> | ||
| + | 8. Press the '''Apply Settings''' button so that the IP address will be assigned to the wireless interface. | ||
| + | [[Image:Unbridged_eth1.jpg]] | ||
| + | === Step 2: Add DHCP for the unbridged WLAN interface === | ||
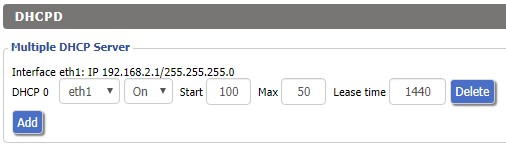
| + | # Press the '''Add''' button in the '''Multiple DHCP Server''' section. | ||
| + | # Select the interface you unbridged in '''Step 1''' in the left drop down menu that appeared. | ||
| + | # Press the '''Apply Settings''' button to finish enabling the DHCP server for the wireless interface. | ||
| + | [[Image:Eth1_DHCP.jpg]] | ||
| + | ''If DHCP is disabled on your main LAN in Basic Setup, then the Multiple DHCP method above will not work. Consult [[Multiple_WLANs#Command_Method|Multiple WLANs]] for instructions on setting up a DHCP server for your unbridged interface using '''Additional DNSMasq Options'''. Note that those instructions set up a DHCP server for a bridge, so you will need to substitute occurrences of '''br1''' with your unbridged interface.'' | ||
| + | You should now be able to connect to the unbridged wireless interface and receive a DHCP lease with an IP address that is in the '''192.168.2.0/24''' subnet. Make sure that you can connect to it, receive a DHCP lease, and connect to the router's '''192.168.2.1''' address before you do anything further. If your WAN port is active (ie. you're not making a WAP) then you should also be able to browse the Internet. If you are making a WAP then you must either use iptables commands for WAP's like in [[Multiple_WLANs#Restricting_Access|Multiple WLANs]], or create routes throughout your network. | ||
| + | === Step 3: Controlling Access === | ||
| + | '''Step 1''' has automatically restricted the unbridged interface from accessing the '''192.168.1.0/24''' subnet (typically the wired LAN). | ||
| + | To also restrict the unbridged interface from accessing another interface, add the following to your Firewall [[Startup_Scripts|Startup Script]]: | ||
| + | iptables -I FORWARD -i <interface> -o <other> -j DROP | ||
| + | where ''<interface>'' is your unbridged interface and ''<other>'' is the interface you don't want it talking to. | ||
| - | + | To prevent devices on the unbridged interface from accessing each other, as well as all other local interfaces, add the following to your Firewall startup script: | |
| - | + | iptables -I FORWARD -i <interface> ! -o <wan_interface> -j DROP | |
| + | where ''<interface>'' is your unbridged interface and ''<wan_interface>'' is the interface your WAN port is assigned to (typically '''vlan2''', see ''Setup>Networking>Port Setup'' to verify. | ||
| - | + | === Additional Wireless Interfaces === | |
| - | + | '''Steps 1-3''' can be repeated as needed to unbridge additional wireless interfaces. Be sure to use a different subnet for each unbridged interface, i.e. you cannot use '''192.168.2.0/24''' for both '''eth1''' and '''eth2'''. | |
| - | + | === Unbridged Interfaces Broken === | |
| - | + | In the rare case that unbridged interfaces do not give WAN access in your build, you may need to create a new bridge, e.g. '''br1''' for your wireless interface. Your instructions will then be more akin to those for [[Multiple WLANs]], assigning real wireless interfaces to the new bridge instead of virtual interfaces. | |
| - | + | ||
| - | + | ||
| - | [ | + | == See Also == |
| - | [ | + | * [[iptables command]] |
| - | [ | + | * [https://forum.dd-wrt.com/phpBB2/viewtopic.php?t=323129 Leaving wireless interface unbridged?] |
| - | [ | + | == Legacy Guides == |
| - | [ | + | * [[Multiple WLANs]] - Using multiple bridges |
| - | + | * [[V24: WLAN separate from LAN, with independent DHCP]] - For v24 | |
| + | * [[WLAN separate from LAN, with independent dhcp, etc]] - Using the CLI | ||
| - | + | [[Category:Interfaces]] | |
| + | [[Category:Wlan]] | ||
| + | [[Category:Lan]] | ||
| + | [[Category:Basic tutorials]] | ||
Current revision
|
English • Deutsch • Español • Français • Italiano • 日本語 • Polski • Português • Русский • Svenska • 中文(中国大陆) • 中文(台灣) • |
Contents |
[edit] Introduction
This guide explains how to separate the wireless interface from the "LAN&WLAN" bridge so that they are on different subnets. You are then able to control communication between the interfaces using iptables commands.
If your router is configured as a Wireless Access Point (WAN is disabled) then you must be sure to set the gateway and local DNS as recommended in the WAP guide. This also applies to WDS client nodes (but not the main WDS node) which are bridged to another router that does routing for them. Keep your eye out for the places this guide gives alternative instructions for WAP's.
Note: If you're separating virtual interfaces then use the instructions from the Multiple WLAN Guide.
[edit] Preparation
Go to the Administration -> Commands page, insert the command below, and press the Run Commands button to find out the actual name of your wl0 interface. If you have a wl1 interface that you want to unbridge then change the command accordingly.
nvram get wl0_ifname
[edit] Configuration
[edit] Step 1: Remove the Wireless Interface from the LAN bridge
1. Navigate to the Setup -> Networking page.
2. In the Port Setup section, find the configuration for the interface (identified in #Preparation) that you would like to unbridge.
3. For that interface, select the Unbridged radio button next to Bridge Assignment. More options will appear.
4. Set Masquerade / NAT to Enable.
5. Set Net Isolation to Enable. This will automatically add a rule like this to your firewall:
iptables -I FORWARD -i <interface> --destination 192.168.1.0/24 -m state --state NEW -j DROP
6. Set an IP Address that is in an unused subnet, e.g. 192.168.2.1.
7. Set the Subnet Mask to 255.255.255.0.
8. Press the Apply Settings button so that the IP address will be assigned to the wireless interface.
[edit] Step 2: Add DHCP for the unbridged WLAN interface
- Press the Add button in the Multiple DHCP Server section.
- Select the interface you unbridged in Step 1 in the left drop down menu that appeared.
- Press the Apply Settings button to finish enabling the DHCP server for the wireless interface.
If DHCP is disabled on your main LAN in Basic Setup, then the Multiple DHCP method above will not work. Consult Multiple WLANs for instructions on setting up a DHCP server for your unbridged interface using Additional DNSMasq Options. Note that those instructions set up a DHCP server for a bridge, so you will need to substitute occurrences of br1 with your unbridged interface.
You should now be able to connect to the unbridged wireless interface and receive a DHCP lease with an IP address that is in the 192.168.2.0/24 subnet. Make sure that you can connect to it, receive a DHCP lease, and connect to the router's 192.168.2.1 address before you do anything further. If your WAN port is active (ie. you're not making a WAP) then you should also be able to browse the Internet. If you are making a WAP then you must either use iptables commands for WAP's like in Multiple WLANs, or create routes throughout your network.
[edit] Step 3: Controlling Access
Step 1 has automatically restricted the unbridged interface from accessing the 192.168.1.0/24 subnet (typically the wired LAN).
To also restrict the unbridged interface from accessing another interface, add the following to your Firewall Startup Script:
iptables -I FORWARD -i <interface> -o <other> -j DROP
where <interface> is your unbridged interface and <other> is the interface you don't want it talking to.
To prevent devices on the unbridged interface from accessing each other, as well as all other local interfaces, add the following to your Firewall startup script:
iptables -I FORWARD -i <interface> ! -o <wan_interface> -j DROP
where <interface> is your unbridged interface and <wan_interface> is the interface your WAN port is assigned to (typically vlan2, see Setup>Networking>Port Setup to verify.
[edit] Additional Wireless Interfaces
Steps 1-3 can be repeated as needed to unbridge additional wireless interfaces. Be sure to use a different subnet for each unbridged interface, i.e. you cannot use 192.168.2.0/24 for both eth1 and eth2.
[edit] Unbridged Interfaces Broken
In the rare case that unbridged interfaces do not give WAN access in your build, you may need to create a new bridge, e.g. br1 for your wireless interface. Your instructions will then be more akin to those for Multiple WLANs, assigning real wireless interfaces to the new bridge instead of virtual interfaces.
[edit] See Also
[edit] Legacy Guides
- Multiple WLANs - Using multiple bridges
- V24: WLAN separate from LAN, with independent DHCP - For v24
- WLAN separate from LAN, with independent dhcp, etc - Using the CLI
Categories: Interfaces | Wlan | Lan | Basic tutorials